Guardium’s SOX Accelerator provides a library of best practices templates for addressing key SOX requirements, such as monitoring the following:
| ˙ |
Privileged user activities |
| ˙ |
Schema changes |
| ˙ |
Privilege changes |
| ˙ |
Database logins |
| ˙ |
Security exceptions such as failed logins and database errors |
The SOX Accelerator is based on the standard COBIT (Control Objectives for Information and Related Technology) framework for IT controls, which has become the de facto standard for SOX auditors and compliance.
Guardium’s SOX Accelerator encompasses all four COBIT domains including:
Plan and Organize Manage the planning phase by gathering information about who is touching your critical financial objects in order to quickly identify unauthorized users and applications.? Using advanced auto-discovery capabilities, the system creates a visual access map showing all database servers, applications, clients, and subnets. Interactive drill-downs enable quick understanding of the “who, what, when, where, and how” of all database transactions, organized by access type, content, and frequency.
Certify and Control Enables users to certify that all database access activities are aboveboard and that those that fall outside of SOX parameters can either be rectified or explored further.? Information provided includes a “to do” list of audit tasks, as well as a variety of reports on topics such as financial system exceptions; failed user logins; user activity audit trails; SQL errors on financial data; and access to financial data by unauthorized applications.? Customizable tests, weights, and assessments provide the flexibility you need for continuous, real-time snapshots and tracking continuous improvement metrics over time.
Assess Risk Offers information that can be used to gauge possible risks, with emphasis on those areas referred to in the database-related requirements for SOX.? These reports cover such categories as users sharing database credentials across multiple client IPs to access financial data; after hours activities on financial database servers; access to financial data by unrecognized users; attempts to access financial data by a non-recognized client; and a variety of commands executed on financial databases.
Investigate and Disclose Dig deeper into any possible exceptions to discover their origins, as well as whether or not there are issues that warrant further handling. Includes reports showing the distribution of DDL and DML commands for financial databases; user activity on financial data, organized by client IP and database user; details about all sessions by financial server IP; detailed activity on financial objects; and more.
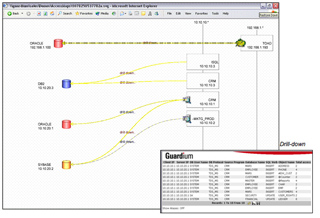

Full Visibility and Understanding
A visual access map allows you to quickly identify unauthorized users and applications with a graphical representation of all database servers, clients, subnets, and applications. Interactive drill-downs enable quick understanding of the “who, what, when , where and how” of all database transactions.

|
