Address Data Leakage at the Core
Most information leaks, even those that occur via stolen laptops or emailing sensitive information, originate with unauthorized or unusual queries to critical databases.? Many organizations have formal access policies that govern how and when sensitive data is accessed, but lack practical solutions for detecting or blocking activities that fall outside these policies.
Unlike Data Leak Prevention (DLP) solutions that watch data as it leaves the network perimeter via email or end-points via USB devices, Guardium’s database leak prevention solution addresses leakage at the data source—in the data center itself—using three essential technologies:
Auto-Discovery and Classification of Sensitive Data: Guardium’s Classifier uses a database crawler to look for patterns such as 16-digit credit card numbers and 9-digit Social Security numbers in corporate databases.? Companies often fail to locate all of their sensitive data, especially after mergers and acquisitions or when using legacy systems.? Our system generates alerts when it locates sensitive data for the first time, helping organizations quickly identify faulty business or IT processes that result in the storage of confidential data, such as magnetic stripe or PIN block information.
By tagging sensitive objects with meta-data classifications, such as “Privacy-Restricted” or “Regulated Record,” organizations can ensure that appropriate access policies and audit processes are always applied to items with similar properties.? Our system automatically assigns customizable, granular access policies to groups of objects, controlling who has access to them, from which applications and locations, at what times, using which SQL commands, etc.
For forensic investigations and e-discovery initiatives, organizations can use Guardium’s rich data mining tools to analyze a verifiable audit trail of historical transaction information for particular events involving specific classes of data.? Audit trails are stored in Guardium’s audit data warehouse and typically involve tens of millions of sessions.
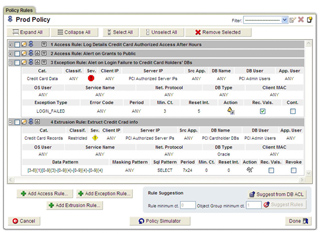
An Extrusion Policy Engine: Unlike monitoring tools that only inspect inbound database commands, the Guardium solution identifies unauthorized or suspicious actions by monitoring traffic both to and from database servers.? This allows our solution to immediately identify, for example, a database query that returns thousands of credit card numbers, thereby deviating from normal operations based on the presence of sensitive data patterns and the volume of returned records.? Information collected by the Extrusion Policy Engine can also be used to understand the true extent of data theft, thus minimizing breach disclosure efforts and costs.
Extrusion Policies are typically used to detect activities by authorized users that fall outside normal business processes.? Guardium also provides access and security exception policies that monitor inbound database commands for unauthorized actions, such as SELECT operations by privileged users or failed logins that fall outside of a given threshold.
Database Intrusion/Extrusion Prevention: Guardium provides technology for real-time enforcement and peremptory blocking of transactions that violate security policies.? This is accomplished by configuring the Guardium system either as an in-line database firewall or as a passive monitoring device that initiates other enforcement actions such as data-level blocking, TCP reset blocking, automated lock-outs of database users, VPN port shutdowns, and real-time alerts

| 