Tighten Change Controls & Increase Staff Efficiency
Most organizations have formal change control policies and processes that govern how and when changes are made to production databases. Until now, however, your IT team may not have had effective tools for detecting when critical changes are made outside of your change control policies and processes.
With Guardium’s solution, you can receive real-time security alerts when changes are made to critical tables or data values. Our system tracks all database changes to:
| ˙ |
Database structures such as tables, triggers, and stored procedures. For example, you can detect accidental deletions or insertions of critical tables that impact data governance and the quality of business decisions. You can also proactively identify malicious acts such as “logic bombs” planted by disgruntled employees |
| ˙ |
Critical data values such as data that affects the integrity of financial transactions |
| ˙ |
Security and access control objects such as users, roles, and permissions. For example, an outsourced contractor could create a new user account with unfettered access to critical databases and then delete the entire account, eliminating all traces of his activity. With Guardium, however, all actions are tracked |
| ˙ |
Database configuration files and other external objects that can affect your database security posture, such as environment/registry variables, configuration files (e.g., NAMES.ORA), shell scripts, OS files, and executables such as Java programs. To accelerate deployment, our Change Auditing System (CAS) provides a library of pre-configured knowledge templates that should be monitored, based on best practices, for all major OS and DBMS combinations |
Best of all, our non-invasive solution monitors all these changes without the performance overhead and complexity of database-resident utilities such as trace logs, transaction logs, or native auditing.
Change Auto-Reconciliation
The Guardium solution enables you to easily automate the time-consuming process of tracking all observed database changes and reconciling them with authorized work orders in your existing change ticketing system, such as BMC Remedy and custom change management applications.
These processes are increasingly required to meet auditors’ requirements, particularly in the context of data governance for SOX.
You can generate real-time, policy-based alerts when unauthorized changes are detected, such as changes made without change control IDs, during production periods, or using unauthorized user IDs.? The Guardium solution also gives you the option of blocking unauthorized changes.
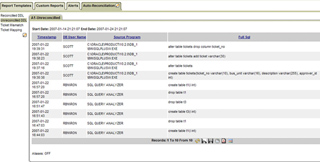

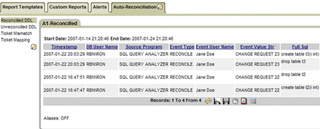

Guardium’s auto-reconciliation capability allows you to track all database changes with ticket IDs from your existing change ticketing system (e.g., BMC Remedy, CA Change Manager, and in-house systems) to quickly reconcile changes with approved work orders.? You can also identify and investigate changes that were made without valid ticket IDs or outside authorized change periods. |
